Introduction
Application Remote Procedure Call (RPC) endpoints can be considered as an essential component of various software systems and services since it enables interaction between different systems and/or services. However, similar to any technology, RPC endpoints are not without problems. Here in this article we are going to discuss some of the frequently faced issues while working with RPC endpoints.
Security Risks
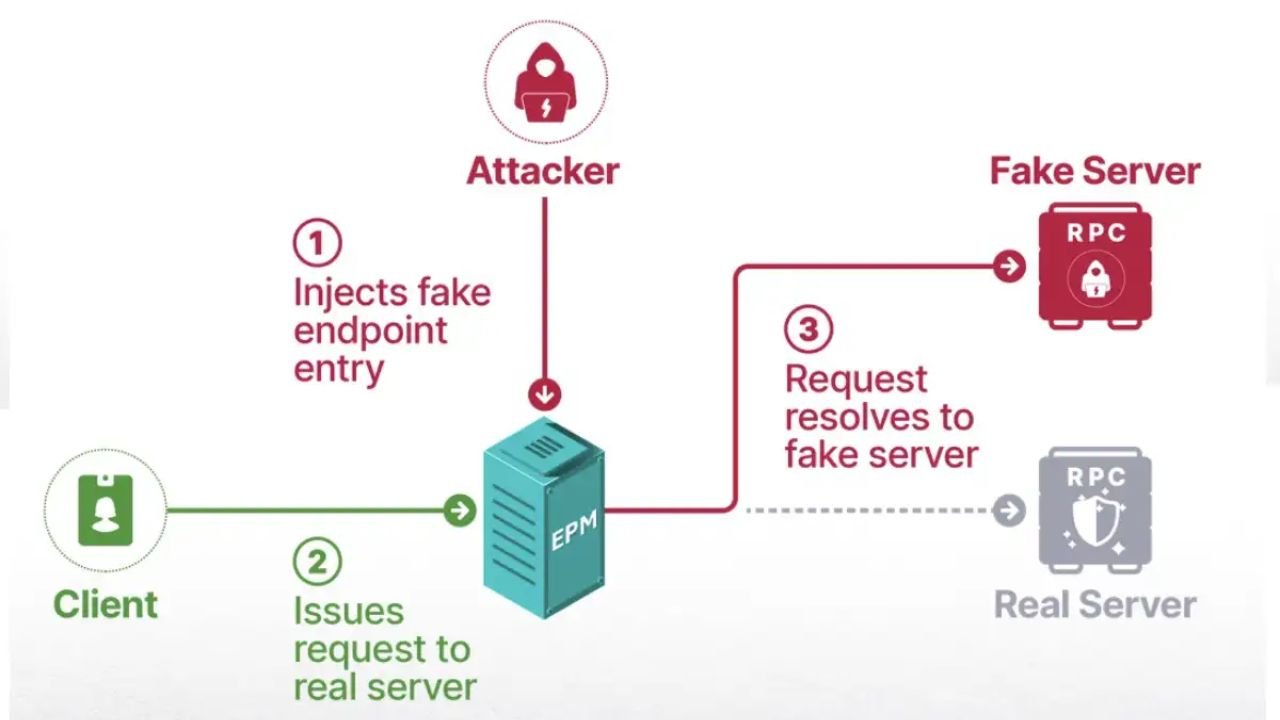
Security is one of the most critical issues related to RPC endpoint. RPC endpoints are primarily at risk because they provide functionality to an outside system. Common security risks include:
- Authentication and Authorization: If authentication and authorization are not implemented properly, then unauthorized access to data and functionality is possible.
- Data Encryption: Transmission of data without encryption is dangerous since it exposes the data to risks such as data leakage and interception.
- Input Validation: One of the biggest mistakes in input validation is resulting in SQL injection and other type of attacks.
Performance Issues
RPC endpoints can also be prone to performance issues, including:
- Latency: This causes delay in the response time and poor experience for the users since they are unable to get the results as quickly as intended.
- Throughput: Throughput can be defined as the rate at which data is processed and transmitted and therefore, low throughput implies that data processing and transmission will be slow.
- Timeouts: Overall, when timeouts are used excessively they cause errors and system crashes.
Compatibility Problems
RPC endpoints can also be susceptible to compatibility issues, including:
- Versioning: Various revisions of the RPC endpoints can cause problems in compatibility and errors can occur.
- Data Formats: Various data formats cause problems and mistakes in data transfer.
- Platform Dependencies: The RPC endpoints that are not platform independent can cause compatibility problem on various systems.
Debugging Challenges
Debugging RPC endpoints can be challenging due to:
- Lack of Visibility: Debugging can be hard if RPC calls can be hard to track and monitor in a program.
- Complexity: If the RPC endpoint implementations are rather complex, then it is difficult to work with problems, finding them and isolating them.
- Logging and Monitoring: Failure to log the application and its usage can create difficulties when analyzing problems.
Best Practices
To avoid these common issues with RPC endpoint example, it’s essential to follow best practices, including:
- Secure Authentication and Authorization: They include strong user authentication to the system as well as secure user access rights.
- Data Encryption: Secure data in motion, as well as in storage.
- Input Validation: Sanitize the data to avoid any form of attacks from the users.
- Monitoring and Logging: Maintain sufficient amounts of monitoring and logging to facilitate the diagnosis of problems.
- Testing and Debugging: Always take time and run a rigorous test on RPC endpoints and debug any issues.
Conclusion
RPC endpoints are a useful way to communicate between systems; however, they are not exempt from several challenges. If these issues are understood and best practices are followed, then strong and secure RPC endpoints can be created to fit the use of a project.